Site menu
Section categories
| PORTABLE SOFTWARE |
| SOFTWARE |
| SARADADDY REPACK GAMES |
| PC GAMES |
| KIDS GAMES |
| VIDEO TUTORIALS |
| MOVIES |
| ANIMATED MOVIES |
| e-BOOKS |
| Hidden Object Games |
| Dash / Time Management |
| Casino Games |
| MAHJONG |
Statistics
Total online: 3
Guests: 3
Users: 0

Main » 2013 November 20 » Acunetix Web Vulnerability Scanner Consultant Edition 9.0.2013.11.07.Retail
11:56:30 Acunetix Web Vulnerability Scanner Consultant Edition 9.0.2013.11.07.Retail |
Acunetix Web Vulnerability Scanner Consultant Edition 9.0.2013.11.07 Retail  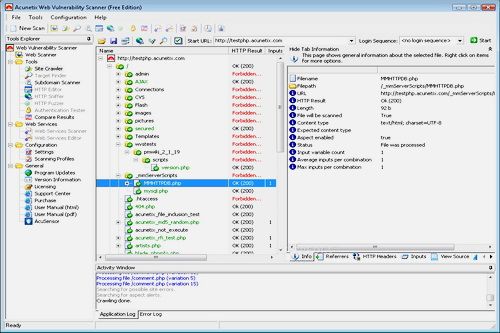 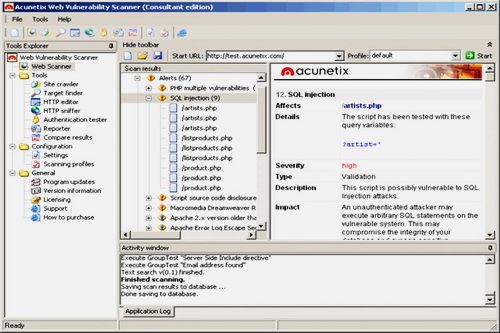 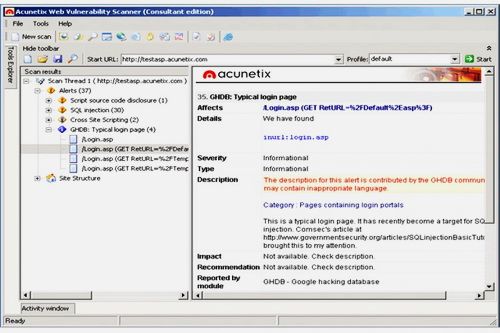 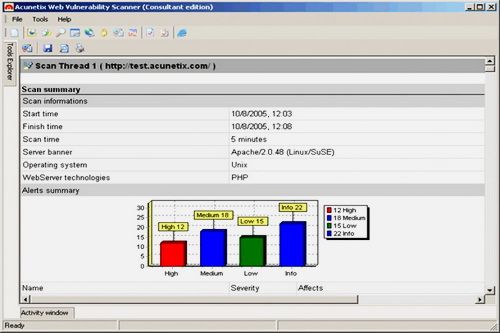 Size : 28 Mb Is Your Website Hackable? ACUNETIX – A world-wide leader in WEB application security Audit your website security with Acunetix Web Vulnerability Scanner v9 As many as 70% of websites have vulnerabilities which could be exploited by hackers or rogue insiders, leading to theft of sensitive corporate data such as credit card information and customer lists. Hackers concentrate their efforts on web-based applications such as shopping carts, forms, login pages, dynamic content and plain-and-simple human error. Accessible 24/7 from anywhere in the world, insecure web applications provide easy access to backend corporate databases and allow hackers to perform illegal activities using the compromised site. The Consultant edition license allows customers to install one copy of Acunetix on one computer, and scan an unlimited number of sites or servers provided that they have obtained permission from the respective site owners. Scanning of third party sites without the necessary permission from their respective owners is prohibited with this license. This Consultant edition is ideal for consultants who provide web security testing services, or an ISP, for example. The Consultant edition also includes the capability of modifying the reports to include their company logo. This edition is the only edition that you can use to audit third-party websites, i.e., websites not owned by the company you are working for. Firewalls, SSL and Locked-Down Servers are futile against WEB Application Hacking! Web application attacks, launched on port 80/443, go straight through the firewall, past operating system and network level security, and right into the heart of your application and corporate data. Tailor-made web applications are often insufficiently tested, have undiscovered vulnerabilities and are therefore easy prey for hackers. FIND OUT IF YOUR WEBSITE IS SECURE BEFORE HACKERS download sensitive data, use your website as a launch pad for criminal activities, or endanger your business. Acunetix Web Vulnerability Scanner v9 crawls your website, automatically analyzes your web applications and finds perilous SQL injection, Cross Site Scripting and other vulnerabilities that expose your online business. Concise reports identify where web applications need to be fixed, thus enabling you to protect your business from impending hacker attacks! Acunetix has pioneered web application security scanning: Its engineers focused on web security as early as 1997 and developed an engineering lead in website analysis and vulnerability detection. • NIST Special Publication 800-53 - Recommended Security Controls for Federal Information Systems • OWASP TOP 10 2013 • Payment Card Industry Data Security Standard version 2.0 • Sarbanes-Oxley Act • DISA STIG Web Security • Web Application Security Consortium: Threat Classification STOP SEARCH ENGINE HACKERS Acunetix launches queries from the Google Hacking Database (GHDB) onto the crawled content of your website, identifying sensitive data or exploitable targets before a search engine hacker does. AUTOMATIC CUSTOM 404 Error Page Identification Automatically determine if a custom error page is in use, and identify it without needing any recognition patterns to be configured before the scan. PORT SCANNING and Network Alerts Acunetix Web Vulnerability Scanner also runs optional port scans against the web server hosting the website and automatically identifies network services running on open ports and launches a series of network security tests against that network services. Customized network alerts can also be developed by following detailed SDK documentation provided by Acunetix. The security checks that ship with the product are: •Test for weak passwords on FTP, IMAP, SQL servers, POP3, Socks, SSH, Telnet and other DNS server vulnerabilities like Open Zone Transfer, Open Recursion, Cache Poisoning, • FTP access tests such as if anonymous access is allowed, and list of writable FTP directories, security checks for badly configured Proxy Servers •Checks for weak SNMP Community String, •Checks for weak SSL ciphers, •And many other sophisticated security checks! ADVANCED PENETRATION Testing Tools In addition to its automated scanning engine, Acunetix includes advanced tools to allow penetration testers to fine tune web application security audits: • HTTP Editor – Construct HTTP/HTTPS requests and analyze the web server response. • HTTP Sniffer – Intercept, log and modify all HTTP/HTTPS traffic and reveal all data sent by a web application. • HTTP Fuzzer – Perform sophisticated fuzzing tests, in order to test web applications input validation and handling of unexpected and invalid random data. Test thousands of input parameters with the easy to use rule builder of the HTTP Fuzzer. Tests that would have taken days to perform manually can now be done in minutes. • Blind SQL Injector – An automated database data extraction tool that is ideal for penetration testers who wish to make further tests manually. More ADVANCED FEATURES • Detect HTTP Parameter Pollution (HPP) vulnerabilities. • Support for custom HTTP headers in automated scans. • Support for multiple HTTP authentication credentials. • Scanning profiles to easily scan websites with different scan options and identities. • Custom report generator. • Compare scans and find differences with previous scans. • Easily re-audit website changes with rescan functionality. • Support for CAPTCHA, Single Sign-On and Two Factor authentication mechanisms. • Detect directories with weak permissions and if dangerous HTTP methods are enabled. • Generate a list of uncommon HTTP responses such as internal server error, HTTP 500, etc. • Customize list of false positives. • Security audit of the web server configuration. • Auto importation of IIS 7 rewrites rules directly from web.config.file. • Ability to rescan a specific vulnerability in order to verify remediation. • Automate File Upload Forms vulnerability testing. Check links with this FILEFACTORY LINK CHECKER  If links are dead, please leave comment in the post.  https://www.filefactory.com/file/63ihfhp0k3rf/n/ |
|
|
| Total comments: 0 | |